Requesting SSL Certificates in ServBay Using the ACME Protocol
ServBay supports the use of the ACME protocol to automatically request SSL/TLS certificates for your local development websites. ACME (Automated Certificate Management Environment) is a standard protocol for automating the certificate lifecycle, including issuance, renewal, and revocation. With the ACME management panel provided by ServBay, you can easily and rapidly configure trusted SSL certificates for your local sites—a crucial capability for simulating production environments and testing HTTPS functionality.
By default, ServBay uses ZeroSSL to issue certificates, but you are free to choose Let’s Encrypt, Google Trust Services, or any other ACME-compatible Certificate Authority (CA).
TIP
To ensure your local development environment mirrors your production setup as closely as possible, using trusted SSL certificates is vital. ServBay’s ACME functionality makes this process exceptionally straightforward.
Key Concepts Explained
Before you start, it helps to understand a few core concepts that will help you make the most of ServBay’s ACME features:
- ACME Protocol: An open standard for automating interactions between Certificate Authorities (CAs) and servers, enabling automatic certificate issuance, renewal, and management.
- DNS-01 Validation (via DNS API): ACME supports multiple domain ownership validation methods. ServBay primarily uses the DNS-01 approach, which requires you to add a specific TXT record to your domain's DNS. The CA verifies the presence and content of this TXT record to confirm your control of the domain. Advantages of DNS-01 validation include:
- Your local development environment does not need to be accessible from the public Internet.
- Validation can complete even if local ports 80/443 are blocked by a firewall or ISP.
- External Account Binding (EAB): For some CAs (like Google Trust Services or ZeroSSL), first-time certificate requests via ACME require EAB to associate your ACME client (here, the acme.sh integration in ServBay) with an account you’ve registered at that CA. This typically involves a Key ID and an HMAC Key.
- ECC vs. RSA Certificates:
- RSA: Traditional encryption algorithm with excellent compatibility, but requires longer keys (e.g., 2048 or 4096 bits) for strong security, resulting in higher computational overhead.
- ECC (Elliptic Curve Cryptography): A modern cryptographic algorithm. For equivalent security, ECC requires much shorter key lengths (e.g., 256 or 384 bits) than RSA. ECC certificates offer higher performance, reduced handshake times, lower bandwidth consumption, and improved forward secrecy. ServBay recommends ECC certificates by default.
Prerequisites
ServBay uses the DNS API method to request ACME certificates, so your local site does not need to be accessible from the Internet. Before applying for an SSL certificate via ACME, make sure you meet the following prerequisites:
- Own a Domain: You need a registered domain over which you have control to manage DNS records.
- Obtain Your DNS Provider’s API Key: During the ACME process, the DNS API is used to automatically add and remove TXT records for validation. Obtain the API Key or relevant credentials from your DNS service provider (the platform hosting your DNS records, which may be different from your registrar). For a list of supported DNS providers and instructions to obtain their API KEYs, visit the acme.sh official Wiki DNS API section (English): How to use DNS API. Look up the appropriate guide for your provider.
- Obtain EAB Information (if using Google Trust Services or ZeroSSL for the first time): If you opt for Google Trust Services, obtain EAB credentials from Google Cloud. Refer to the official documentation (English): Obtaining EAB credentials from Google Cloud. For ZeroSSL, you may also need email verification or an API Key for your first request.
Requesting an SSL Certificate via ACME in ServBay
Follow these steps to request an SSL certificate for your local development site in ServBay with ACME:
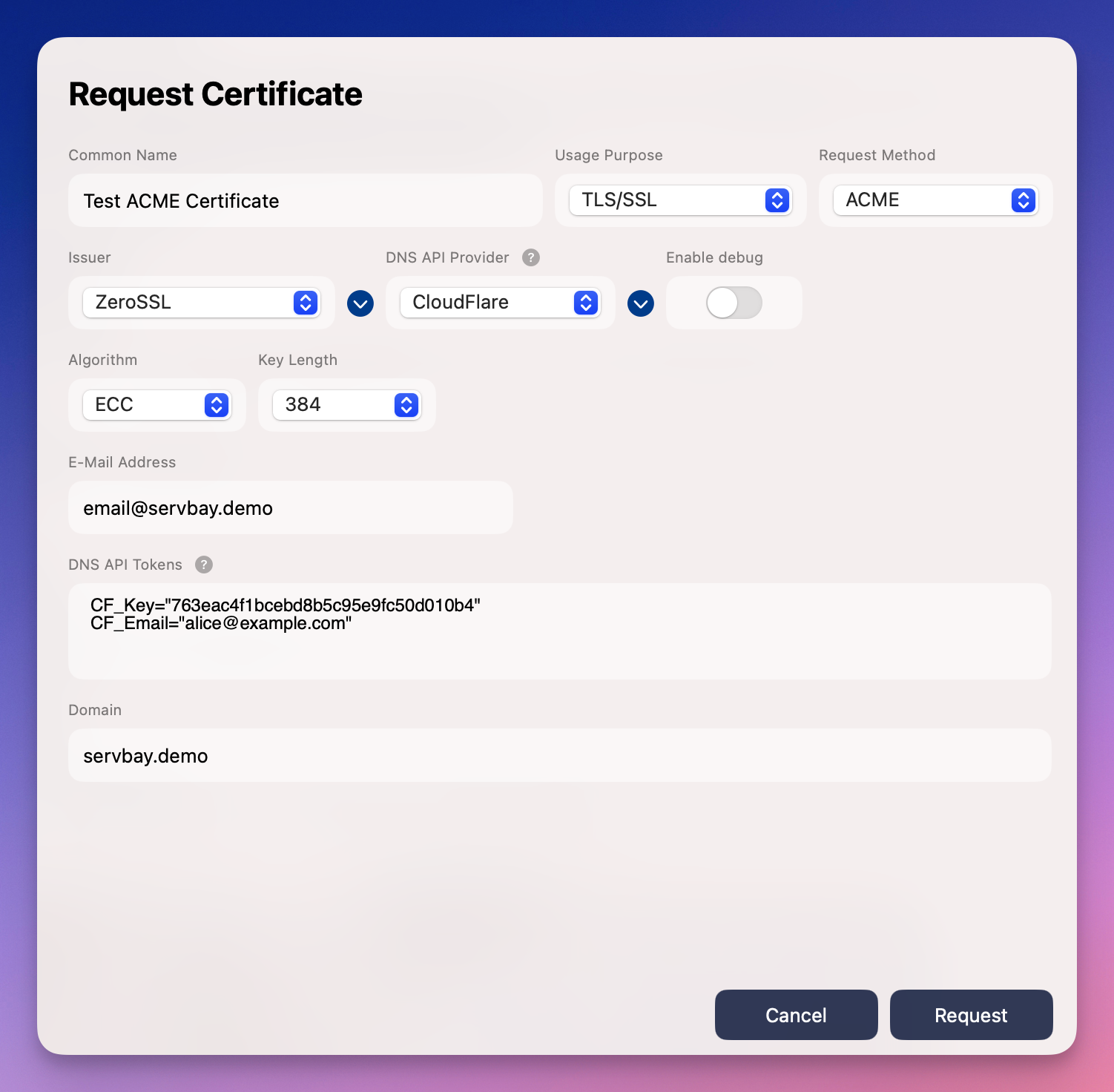
Open the ServBay Management Panel Launch the ServBay app and access its management panel via the system menu bar or Dock icon.
Navigate to SSL Certificate Management In the left sidebar, click on
SSL Certificates.Start a New Certificate Request In the top-right corner of the SSL Certificates management screen, click the
+button and selectRequest New Certificate.Configure Certificate Details
- Certificate Name: Enter a descriptive name for easy identification (e.g.,
servbay-demo-ssl). - Use Case: Select
TLS/SSL. - Request Method: Select
ACME.
- Certificate Name: Enter a descriptive name for easy identification (e.g.,
Select the Certificate Authority (CA) In the
Issuerdropdown, choose your preferred CA. By default, it’sZeroSSL, but you can selectLet’s EncryptorGoogle Trust Services. This guide usesZeroSSLas an example.Choose DNS API Provider In the
DNS API Providerdropdown, select your domain’s DNS service platform. Here we useCloudflareas an example. Make sure to select the DNS hosting platform, not necessarily your registrar if they’re different.Choose Certificate Algorithm & Key Length
- Algorithm: ECC is recommended by default for better performance and security, but select RSA if compatibility with legacy devices is needed.
- Key Length: For ECC, the default is usually
384bits—plenty secure. For RSA,2048or4096bits are common.
Enter Validation Information Depending on your chosen CA and DNS API Provider, the necessary input fields will appear.
- For ZeroSSL, you may need to enter your email address.
- For Cloudflare’s DNS API, input your API Key or authentication details as required by the acme.sh Wiki for your provider.
WARNING
Note: Paste only the actual API Key or secret value—do not include
exportor other shell command prefixes in the input field.Set Domain Name Enter the domain for which you want the certificate (e.g.,
servbay.demoor*.servbay.demo). For wildcard certificates, ensure your DNS provider supports automated TXT record management for wildcards.Submit Your Request Once all information is correctly filled in, click the
Requestbutton. ServBay will invoke the integratedacme.shtool with your DNS API credentials to automatically validate the domain and request the certificate from the CA.
The request process may take some time, depending on DNS record propagation and the CA’s response speed. You can track progress in ServBay’s logs or the certificates list. Once successful, your newly issued certificate will appear in the SSL Certificates list.
Applying Certificates in ServBay Site Configuration
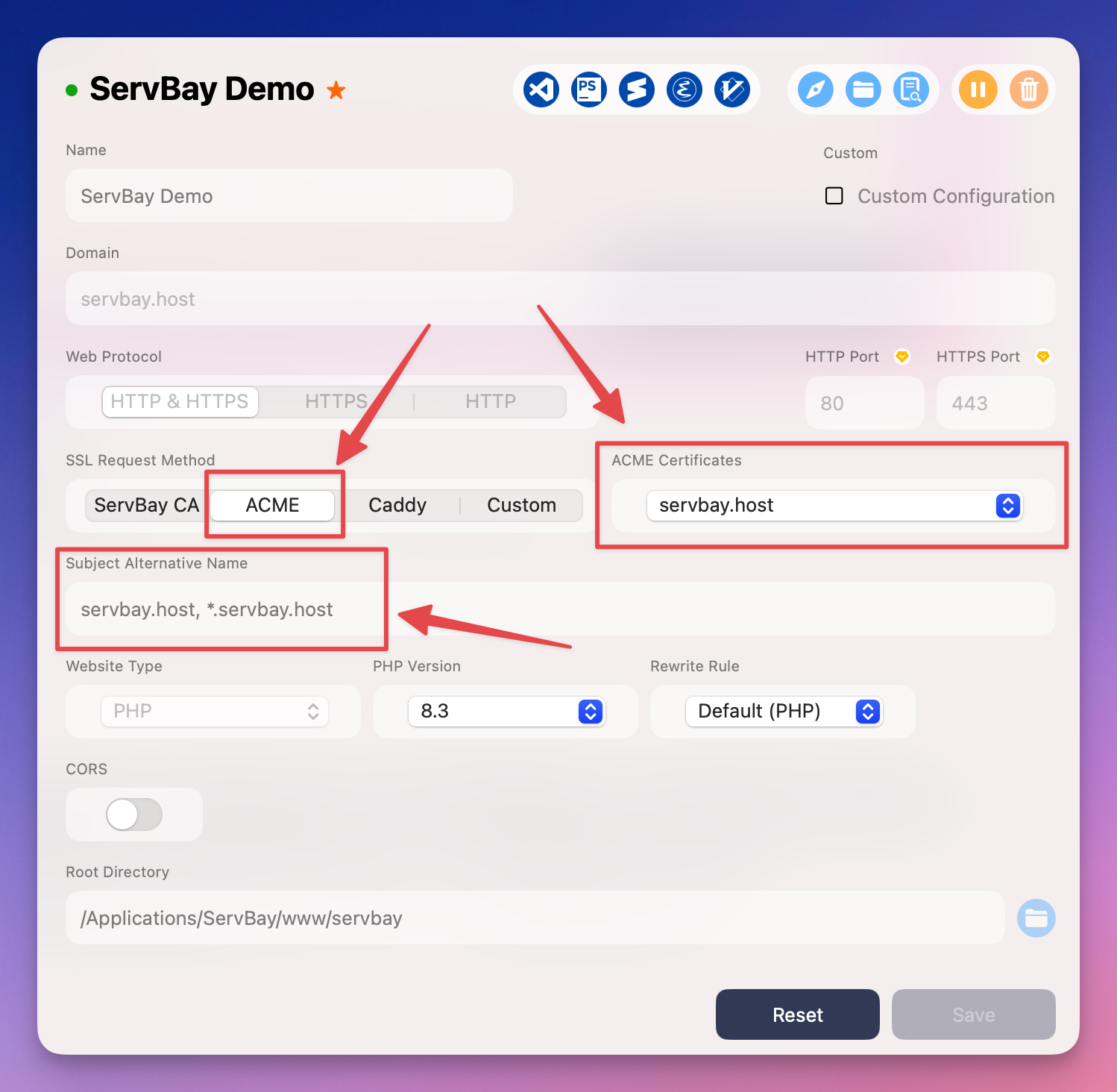
After obtaining your ACME certificate, apply it to your sites configured in ServBay:
- In the ServBay management panel sidebar, select
Sites. - Choose the site for which you want to configure SSL and click the edit button (pencil icon) on the right.
- On the site configuration details page, find the
SSL Certificateoption. - Select the ACME certificate you just issued from the dropdown menu.
- Make sure the
Enable SSLtoggle is switched on. - Save the site configuration. Your site should now be accessible over HTTPS.
ACME Certificate Renewal
Certificates issued via ACME (e.g., from Let’s Encrypt or ZeroSSL) are typically valid for 90 days. To ensure continuous HTTPS access, certificates must be renewed before expiration.
ServBay automatically monitors all ACME-obtained certificates. As a certificate approaches its expiration date, ServBay will attempt renewal with the previously provided DNS API details.
As long as your DNS API credentials remain valid and your DNS service is running smoothly, you do not need to take manual action. ServBay will renew certificates for you in the background.
FAQ & Troubleshooting
- Request failed with DNS validation errors?
- Double-check your DNS API credentials for correctness and sufficient permissions to modify TXT records.
- Ensure that the DNS API provider you selected in ServBay matches the actual platform managing your domain’s DNS.
- After adding DNS records, allow some time for DNS changes to propagate globally—it may take several minutes or longer. Try again later if necessary.
- Check that your domain name spelling is correct.
- Failure with EAB-related error?
- For first-time requests with Google Trust Services or ZeroSSL, ensure you’ve correctly obtained and entered EAB credentials.
- If you previously succeeded but now fail, your EAB credentials may be expired or invalid; obtain fresh ones as needed.
- Error message: “Rate Limit Reached”?
- CAs limit the number of certificates you can request for each domain or from a single IP within a set period. If you make repeated or bulk requests, rate limits can trigger. Wait several hours or days before retrying.
- Certificate issued successfully, but browser still shows insecure?
- Confirm that you’ve correctly applied the new certificate to your site’s configuration in ServBay and that SSL is enabled.
- Try clearing your browser cache or use Incognito/Private mode.
- Check that your local hosts file or network configuration points properly to ServBay.
- When does ServBay attempt automatic renewal? ServBay generally starts attempting automatic renewal a certain number of days before the certificate expires (e.g., 30 days). As long as the ServBay app is running and has network access, renewal happens quietly in the background.
Conclusion
ServBay delivers powerful yet easy-to-use ACME features, allowing developers to conveniently request and manage trusted SSL/TLS certificates for their local development sites using the DNS API method. This not only simplifies certificate configuration but—more importantly—enables a local development environment that closely resembles production and supports HTTPS, helping you develop and test more effectively.
We hope this guide helps you successfully configure SSL certificates in ServBay using the ACME protocol, enhancing your local development workflow.