ServBay SSL Certificate Support and Usage
SSL certificates are essential for modern websites and applications. They encrypt connections, protect user data, and increase trust in your site. Enabling HTTPS in local development is just as important—it simulates a production environment, helps uncover potential security issues, and ensures features that rely on secure connections (like Service Workers and HSTS) function properly. ServBay provides robust SSL certificate support, allowing you to easily manage and deploy various types of certificates locally, ensuring your development and testing environments are safe and reliable.
Purpose and Importance of SSL Certificates
SSL certificates (more precisely, TLS/SSL certificates) secure sensitive data by establishing an encrypted connection between your server and client (such as a web browser). They also validate server identity, protecting users against malicious phishing sites. Using SSL/HTTPS in local development offers several key benefits:
- Data Encryption: Safeguard sensitive data in your local testing environment and simulate secure data transfers as in production.
- Authentication: Locally verify that you’re accessing the intended development site, not an unintended resource.
- Production Environment Simulation: Many modern web features and services (such as Geolocation API, WebRTC, Service Workers in Progressive Web Apps (PWA), etc.) require a secure context (HTTPS) to run. Enabling HTTPS locally ensures these features work correctly during development.
- Avoid Browser Warnings: Using valid (even if self-signed and locally trusted) SSL certificates for local testing prevents "insecure connection" browser warnings and ensures a smoother development experience.
- SEO Optimization (Production): While primarily important for production, understanding this helps developers build with security in mind. Search engines like Google favor HTTPS sites and use it as a ranking factor.
Types of SSL Certificates and Issuance Methods Supported by ServBay
ServBay supports a range of SSL certificate types and issuance methods to suit different development and testing requirements:
Supported Certificate Authorities (CAs) / Issuance Methods
- ServBay User CA: A local user-level CA provided by ServBay, designed for quick and easy generation of self-signed certificates—ideal for local development and testing. These certificates are not trusted by public browsers by default, but can be locally trusted by installing the ServBay User CA root certificate into your OS.
- ServBay Public CA: ServBay’s public CA service issues certificates that are trusted by users who have installed the ServBay Public CA root certificate—perfect for team sharing or limited-scope production use.
- ACME Protocol Support: ServBay offers full support for the ACME protocol, enabling automated certificate issuance and renewal from ACME-compatible CAs, such as:
- Let's Encrypt: A free, automated CA widely used in production. ServBay offers integrated support for easy issuance and renewal of Let's Encrypt certificates.
- ZeroSSL: Another free CA supporting ACME, also integrated with ServBay.
- Google Trust Services: A free CA by Google with ACME support, also integrated with ServBay.
- Third-Party CA Certificates: You can upload and manage certificates purchased or obtained from other trusted third-party CAs (like DigiCert, Sectigo, etc.).
Types of Certificates Managed by ServBay
In addition to domain certificates (TLS/SSL) for securing web traffic, ServBay’s certificate management also supports other certificate types for different purposes:
- Code Signing Certificates: Used to validate developer identity and code integrity, preventing the spread of malicious software. ServBay supports code signing certificate management.
- Email Signing Certificates (S/MIME): Digitally sign and encrypt emails, ensuring authenticity and confidentiality. ServBay supports S/MIME certificate management.
- Document Signing Certificates: Digitally sign documents to ensure their authenticity and integrity. ServBay supports document signing certificate management.
Note: When configuring a website in ServBay for HTTPS, you mainly use domain certificates (TLS/SSL). Management of other types (code signing, S/MIME, document signing) is an extra convenience and not directly related to website HTTPS configuration.
Highlights of ServBay’s SSL Certificate Management
ServBay offers a suite of convenient SSL certificate management features to simplify enabling HTTPS in local environments:
- Automatic SSL Certificate Generation When Creating a Website: When you create a new Website in ServBay, the system can automatically generate and deploy an SSL certificate for it using the ServBay User CA. This streamlines initial setup, ensuring all new local sites are HTTPS-enabled by default with no manual steps.
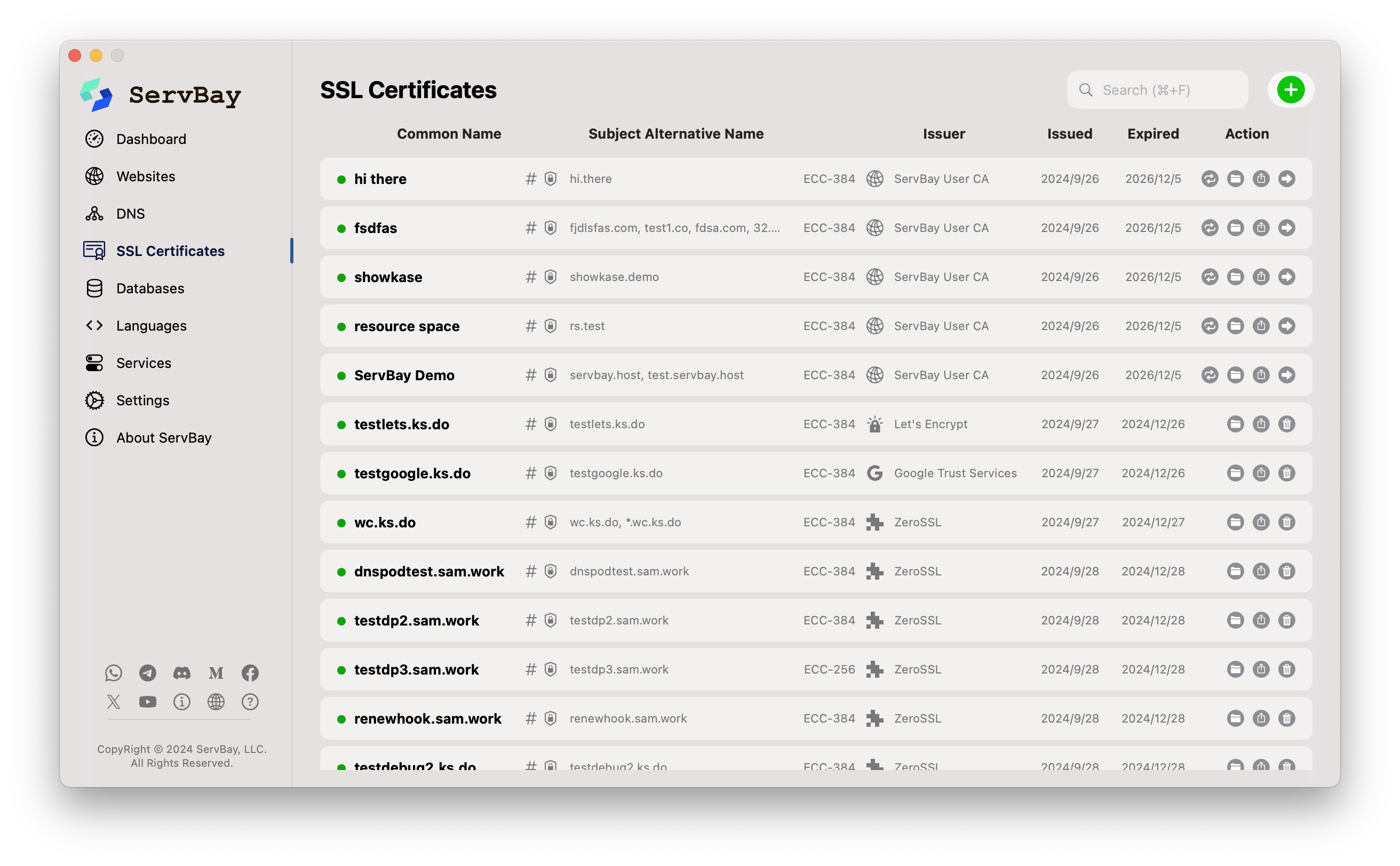
- Graphical Interface Management: ServBay provides an intuitive graphical user interface where you can easily view, import, export, delete, and manage your SSL certificates.
- Automated ACME Issuance and Renewal: With the built-in ACME client, you can apply for certificates from Let's Encrypt, Google Trust Services, or ZeroSSL for your local or public domains directly within the ServBay UI and set up automatic renewal—no manual intervention needed.
- Support for Importing Third-Party Certificates: If you already have certificates from another CA (in
.crt,.key,.pfx, etc. formats), you can import and apply them to your sites through the ServBay interface. - ServBay CA Root Certificate Management: ServBay provides a user-friendly entry in
Settingsto guide you through installing ServBay User CA and ServBay Public CA root certificates into your OS/browser trust store, ensuring local trust and preventing browser warnings.
Difference and Use Cases: ServBay User CA vs. ServBay Public CA
ServBay offers two proprietary CA services, each suited to different situations:
- ServBay User CA:
- Purpose: Tailored for individual ServBay users to quickly generate self-signed certificates for local development and testing.
- Trust: Not trusted by public browsers by default. You must manually install the ServBay User CA root certificate into your OS or browser for local trust, so certificates for domains like
https://servbay.demoorhttps://your-project.servbay.demoshow up as secure (green lock) in your browser. - Use Case: Day-to-day local development and testing by individual developers.
- ServBay Public CA:
- Purpose: Provides the ServBay user community with a mutually trusted certificate source.
- Trust: Requires you to install the ServBay Public CA root certificate for trust. Once installed, all certificates issued by ServBay Public CA are trusted in that environment.
- Use Case: Internal team-shared development/testing, or small-scale, controlled production environments, ensuring local/internal services share trusted HTTPS connections within a team.
How to Trust ServBay User CA Certificates:
To have your browser trust certificates issued by the ServBay User CA on your local machine, add the ServBay User CA root certificate to your OS trust store. When installing ServBay, the ServBay User CA and ServBay Public CA root certificates are automatically added and trusted for the user.
If, for any reason, the ServBay CA root certificates aren’t trusted, you can reinstall and trust them within ServBay’s Settings. Once installed, browsers will no longer display certificate warnings when accessing local sites secured by ServBay User CA certificates.
How to Use SSL Certificates in ServBay (Examples)
Here are some common scenarios for configuring SSL certificates in ServBay:
Create a new website and automatically use ServBay User CA certificate:
- Open the ServBay application.
- Go to the “Websites” management panel.
- Click the button to add a new site.
- Enter the domain (e.g.,
myproject.servbay.demo), and set the site root (e.g.,/Applications/ServBay/www/myproject). - Ensure “HTTP & HTTPS” or “HTTPS” is selected (ServBay will use the ServBay CA by default).
- Save the settings. ServBay will automatically generate a certificate and configure your web server (Caddy, Nginx, or Apache) to use HTTPS.
Configure a ServBay User CA certificate for an existing site:
- Go to the “Websites” management panel.
- Select the site you want to configure.
- Edit its settings and select “HTTP & HTTPS” or “HTTPS”.
- Choose to use a ServBay CA for certificate issuance. If the certificate doesn’t exist, ServBay will generate it automatically.
- Save your changes and restart the web server.
Use the ACME protocol to obtain a certificate from Let's Encrypt, ZeroSSL, or Google Trust Services:
- Go to ServBay’s Certificate Management UI and click the "+" button in the top-right corner.
- Select to apply for a certificate via the ACME protocol.
- Enter the domain you want a certificate for (must be a publicly accessible domain, as ACME requires domain ownership validation).
- Choose an ACME provider (Let's Encrypt, ZeroSSL, or Google Trust Services).
- Follow the UI prompts to select validation type and enter verification details (DNS-01 challenge).
- Once issued, assign the certificate to the corresponding site in ServBay. ServBay also supports ACME certificate auto-renewal.
Notes
- Trusting Root Certificates: When using ServBay User CA or ServBay Public CA certificates, you must install the appropriate root CA into your local operating system, or browsers will show untrusted warnings. ServBay makes this easy from the
SettingsUI. - ACME Challenges: Most local development environments are not publicly exposed for security. ACME certificate issuance (e.g., Let's Encrypt) requires DNS API-based validation. See How to use DNS API for details.
- Certificate Validity Period: Most public CA certificates are time-limited (e.g., Let's Encrypt certificates are valid for 90 days). Make sure to renew in time. ServBay supports automatic renewal for ACME certificates. ServBay User CA certificates typically have a longer validity period.
Frequently Asked Questions (FAQ)
Q: Why does my local ServBay website display a “Not secure” or certificate warning in the browser even when HTTPS is enabled?
A: This is usually because your site uses a certificate issued by the ServBay User CA, and the root certificate hasn’t been trusted by your operating system or browser. The ServBay User CA is a local, non-public CA. To resolve, go to ServBay’s Settings, find the option to install the ServBay User CA root certificate, and follow the prompt to add it to your system trust store. Restart your browser, and you’ll see a secure connection.
Q: Is every user's ServBay User CA the same? Could another user issuing a certificate with their ServBay User CA cause security issues on my machine?
A: There are no security concerns. Each user's ServBay User CA and private key are completely unique. ServBay User CA is issued and managed locally for each user during ServBay installation. If you uninstall and reinstall ServBay, a brand new ServBay User CA and private key are generated and the old ones become invalid.
Summary
ServBay offers web developers comprehensive and easy-to-use SSL certificate support. Whether you need to quickly enable HTTPS for local development, manage ACME-obtained public certificates, or import third-party certs, ServBay has you covered. With automated certificate generation, intuitive management, and support for multiple issuance methods, ServBay greatly simplifies securing connections in your local web development environment—so you can focus on building powerful applications.