Guide to Configuring frp Reverse Proxy Service in ServBay
frp (Fast Reverse Proxy) is a high-performance reverse proxy application that allows you to securely expose your local network services to the public internet. ServBay integrates the frp client (frpc), enabling you to connect to your own deployed frp server (frps), and access local sites hosted in ServBay via custom domains. This setup gives you full control over the tunnel server.
This guide provides step-by-step instructions on configuring the frp client within ServBay and connecting to your frps server.
Overview
Unlike other hosted tunnel services in ServBay, using frp requires you to pre-deploy and configure the frps server on your own server. ServBay acts as the frpc client, forwarding local site traffic through the frps server to the public network. This mode is ideal for developers who demand greater customization and control over their tunnels.
Use Cases
- Full control over the tunnel server: You have complete authority over the configuration, security, and performance of the frps server.
- Use custom domains and SSL: Flexibly configure any domain you own for your local projects and integrate with ServBay-managed ACME SSL certificates.
- Advanced networking configurations: frp supports multiple proxy types and advanced configurations to meet complex needs.
- Private deployment: Ideal when you don't want to rely on third-party tunneling services.
Prerequisites
- ServBay Installed: Ensure your macOS system has ServBay successfully installed and running.
- Self-hosted
frpsserver:- You must have a publicly accessible server where you have successfully deployed and are running the
frpsservice. - Note down the public IP address or domain name of your
frpsserver. - Record the
bindPort(the port for frp client-server communication) andtoken(authentication token) set in thefrpsserver's configuration file (frps.tomlorfrps.ini).
- You must have a publicly accessible server where you have successfully deployed and are running the
- Domain Name and DNS Configuration:
- You need a public domain (e.g.,
your-frp-server.com) and must create an A record in DNS pointing to yourfrpsserver's public IP. This domain will be used to access your local site later.
- You need a public domain (e.g.,
- ACME SSL Certificate in ServBay:
- To enable HTTPS access to your external domain, you need to apply for an ACME SSL certificate for that external domain in ServBay's SSL Certificates section in advance. For example, if you plan to use
project.your-frp-server.comfor accessing your local site, apply for a certificate forproject.your-frp-server.com.
- To enable HTTPS access to your external domain, you need to apply for an ACME SSL certificate for that external domain in ServBay's SSL Certificates section in advance. For example, if you plan to use
- Multiple Subdomains and SSL Certificates:
- If you want to use multiple subdomains without adding multiple DNS A records, you can use a wildcard domain: add an
Arecord for*.your-frp-server.compointing to yourfrpsserver's public IP. Also, in ServBay, apply for an ACME SSL certificate covering the wildcard domain (when applying, enteryour-frp-server.com, *.your-frp-server.comin theDomainfield—make sure the wildcard entry is last and separate each by a comma). Afterwards, you can add any second-level domain in ServBay and share a single SSL certificate, without managing numerous A records. - With this method in ServBay, you can offer external access via domains such as
company-project.your-frp-server.com,personal.your-frp-server.com, andcustomer-1.your-frp-server.com, without repetitive setup.
- If you want to use multiple subdomains without adding multiple DNS A records, you can use a wildcard domain: add an
Step-by-Step Instructions
1. Install the frp Package in ServBay
- Open the ServBay application.
- In the left sidebar, click on Packages.
- In the package list, find
frp. - Click the install button next to
frp. - After installation, the frp service may fail to start due to a lack of configuration—this is expected.
2. Prepare Your frps Server and Configuration
You need to independently install and run frps on your public server. ServBay can generate a basic frps.toml (recommended for newer frp versions) configuration template to help you get started:
In ServBay, navigate to Tunnel -> frp.
Locate and click the dropdown or expand icon next to frp server config (frps.toml).
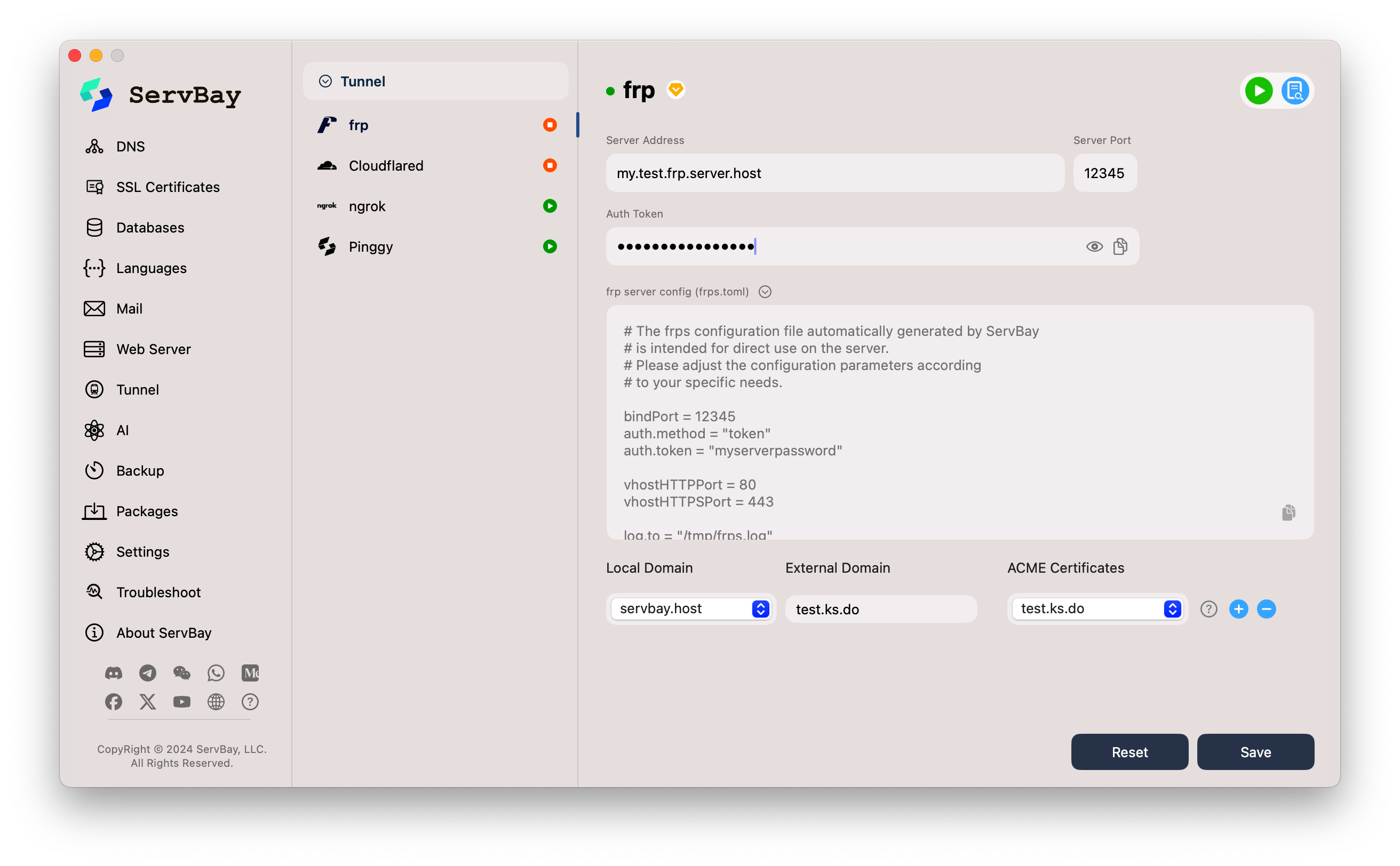 ServBay will display a sample
ServBay will display a sample frps.tomlconfig file, similar to:toml# The frps configuration file automatically generated by ServBay # is intended for direct use on the server. # Please adjust the configuration parameters according # to your specific needs. bindPort = 12345 auth.method = "token" auth.token = "myserverpassword" vhostHTTPPort = 80 vhostHTTPSPort = 443 log.to = "/tmp/frps.log" log.level = "info" log.maxDays = 3 log.disablePrintColor = true # For newer frps versions (e.g., 0.52.0+), configure the Dashboard using webServer.port, webServer.addr, webServer.user, and webServer.password # webServer.port = 7500 # webServer.addr = "0.0.0.0" # webServer.user = "admin" # webServer.password = "admin_password"1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21Important Configuration Notes:
bindPort: The port for frpc to communicate with frps. Ensure this port is open in your server's firewall. It is highly recommended to protect this port on your frps server, for example by using firewall rules to restrict incoming IPs.auth.method = "token"andauth.token: Used for authenticating client connections. Be sure to change to your own strong password.vhostHTTPPort = 80andvhostHTTPSPort = 443: The ports frps will use to listen for HTTP and HTTPS virtual host requests.- [Key Point] ServBay is optimized for scenarios where the frps server uses ports 80 and 443 directly for
vhostHTTPPortandvhostHTTPSPort. This allows seamless pass-through of ACME SSL certificates issued locally in ServBay to frps for client access. - If your frps server cannot use ports 80/443 directly (e.g., occupied by other services) and must use alternative ports (such as 8080/8443), you must deploy an additional reverse proxy server (like Nginx or Caddy) in front of frps. The reverse proxy listens on public ports 80/443 and forwards traffic to the actual
vhostHTTPPortandvhostHTTPSPortof frps. In this setup, SSL certificates will be handled by the reverse proxy, not through ServBay pass-through.
- [Key Point] ServBay is optimized for scenarios where the frps server uses ports 80 and 443 directly for
log.to: The path to the frps log file.- Dashboard settings (e.g.,
webServer.port): For accessing the frps Dashboard UI. Optional.
Copy the generated config content to your
frpsserver, save it asfrps.toml(orfrps.ini, depending on your frp version and preference), and adjust the parameters as needed.Start your
frpsservice.
3. Configure the frp Client in ServBay
Back in the ServBay app, configure the frp client connection parameters:
Navigate to Tunnel -> frp.
Fill in your frps server details:
- Server Address: Enter the public domain or IP of your frps server (e.g.,
my.test.frp.server.host). - Server Port: Enter the
bindPortyou set infrps.toml(e.g.,12345). - Auth Token: Enter the
auth.tokenvalue from yourfrps.toml(e.g.,myserverpassword).
- Server Address: Enter the public domain or IP of your frps server (e.g.,
Set up tunnel mapping rules:
- Local Domain: Select from the dropdown which local ServBay website you'd like to expose via frp (e.g.,
servbay.demo). - External Domain: Enter the domain you want public users to access your local site with (e.g.,
test.ks.do). This domain's DNS A record should already point to your frps server's IP.- Note: Unlike other tunnels ServBay supports (such as
NgrokorCloudflared), you must enter the full domain name here.
- Note: Unlike other tunnels ServBay supports (such as
- ACME Certificates: Select from the dropdown the ACME SSL certificate you have applied for in ServBay for the above external domain (e.g., choose the certificate for
test.ks.do).- Important: If you want HTTPS access for the external domain, you must select the correct certificate here. ServBay will pass this certificate information to frpc, which, after connecting with frps, will ensure frps serves HTTPS requests for the
External Domainusing that certificate. This means you do not need to configure a separate SSL certificate for the external domain directly on your frps server; ServBay handles this.
- Important: If you want HTTPS access for the external domain, you must select the correct certificate here. ServBay will pass this certificate information to frpc, which, after connecting with frps, will ensure frps serves HTTPS requests for the
- Local Domain: Select from the dropdown which local ServBay website you'd like to expose via frp (e.g.,
Add More Tunnels:
- To create tunnels for multiple local sites or external domains, click the
+button next to an existing tunnel entry to add a new tunnel configuration.
- To create tunnels for multiple local sites or external domains, click the
4. Save Configuration and Start frp Service
- After completing all settings, click the Save button at the bottom right corner.
- ServBay will save the frpc configuration and attempt to start the frp service.
- Monitor the status indicator next to
frpunder Tunnel. If configured correctly and frpc connects successfully to frps, the indicator should turn green, showing the service is running. - Verify Access:
- You should now be able to access your local site from the public internet via the configured
External Domain(e.g.,https://test.ks.do). - Click the copy or browser icon next to the external domain to test access.
- You should now be able to access your local site from the public internet via the configured
Notes
- Deployment and Maintenance of
frpsServer: You are solely responsible for installing, configuring, hardening, and maintaining thefrpsserver. - Security for
frpsbindPort: Always use a strongauth.token, and consider using firewall rules to restrict access to thebindPort(e.g., only specific IPs or ranges). - Choice of
vhostHTTPPortandvhostHTTPSPort:- Strongly recommended: let frps listen on ports 80 and 443 directly as virtual host ports. This makes it easiest to take advantage of ServBay’s ACME SSL pass-through functionality.
- If frps must use ports other than 80/443, you will need an additional reverse proxy (such as Nginx or Caddy) running in front of frps listening on 80/443 and forwarding traffic to the actual vhost ports. In this setup, SSL certificates are handled by the front-end proxy.
- ACME Certificate Requirement: To enable HTTPS for your external domain, you must apply for an ACME certificate for that domain in ServBay and select it correctly in the frp configuration.
- DNS Propagation: Ensure the DNS A record of your
External Domaincorrectly points to the frps server's IP and has propagated globally.
Frequently Asked Questions (FAQ)
- Q: The frp service in ServBay fails to start, and the status indicator is red or orange. What should I do?
- A: Check the frp configuration in ServBay: ensure
Server Address,Server Port, andAuth Tokenexactly match thebindPortandauth.tokenin yourfrps.toml. Verify your frps server is running and that thebindPortis accessible from the ServBay machine (check firewall rules). Check the frp service logs for detailed error information.
- A: Check the frp configuration in ServBay: ensure
- Q: I can access through
External Domain, but only over HTTP, not HTTPS?- A: Make sure you have selected the correct ACME certificate for the
External Domainin ServBay's frp configuration. Also, ensure that yourfrps.tomlsetsvhostHTTPSPortto the port on which frps actually listens for HTTPS requests (recommended: 443).
- A: Make sure you have selected the correct ACME certificate for the
- Q: My
frpsserver must use non-80/443 ports for virtual hosts. How do I configure SSL?- A: You need to set up a front-end reverse proxy (such as Nginx or Caddy) on your frps server. This reverse proxy should listen on public ports 80/443, obtain and configure SSL certificates (these can be managed independently from ServBay), and then forward HTTPS traffic (decrypted or encrypted, depending on configuration) to the actual
vhostHTTPSPortof frps. In this scenario, theACME Certificatesfield in ServBay’s frp settings is not used for serving public SSL—SSL is handled by your front-end proxy (NginxorCaddy).
- A: You need to set up a front-end reverse proxy (such as Nginx or Caddy) on your frps server. This reverse proxy should listen on public ports 80/443, obtain and configure SSL certificates (these can be managed independently from ServBay), and then forward HTTPS traffic (decrypted or encrypted, depending on configuration) to the actual
- Q: The
frps.tomlgenerated by ServBay is different from my existingfrps.ini?- A: frp is migrating from
.inito.tomlconfiguration. The template from ServBay uses the.tomlformat. If your frps version is older or you prefer.ini, refer to the official frp documentation for conversion or configuration. The core parameters have the same meaning.
- A: frp is migrating from
Summary
By integrating the frp client, ServBay provides macOS developers who require advanced custom NAT traversal solutions with a powerful toolkit. By self-hosting your frps server and leveraging ServBay’s streamlined frpc configuration and ACME SSL certificate management, you can securely and flexibly share your local development sites with the public internet. Be sure to configure frps and frpc parameters carefully, especially ports and security settings, to ensure stability and safety for your service.