How to Apply for and Use ServBay Code Signing Certificates
Overview
During software development and distribution, code signing is a critical step to establish user trust and ensure software integrity. By digitally signing your code, developers can prove the origin of the software and guarantee that the code hasn’t been tampered with since it was signed.
ServBay provides a convenient feature that allows developers to apply for and use code signing certificates issued by ServBay’s internal CA within their local environment. These certificates are particularly useful for:
- Signing software during local development or testing, simulating the real-world signing process.
- Signing scripts, tools, or applications used internally so their source and integrity can be validated within a team or trusted environment.
- Learning and practicing the entire code signing workflow without having to purchase expensive commercial code signing certificates.
Important Note: Code signing certificates issued by ServBay’s internal CA are not provided by publicly trusted Certificate Authorities (e.g., Let’s Encrypt, Comodo, etc.). They will not be trusted by public operating systems or browsers by default. Therefore, these certificates are not suitable for scenarios requiring public trust, such as distributing commercial software to end users, submitting apps to app stores, or passing OS security checks (e.g., macOS Gatekeeper warnings about unknown developers). They are mainly intended for local development, testing, or use in controlled environments.
Introduction to Code Signing Certificates
A code signing certificate is a digital certificate used to digitally sign executable files, scripts, libraries, and other software code. Its primary functions are to establish trust and enhance security:
- Verifying Publisher Identity: The certificate contains publisher information, and the digital signature can prove that the software genuinely originates from the developer or organization identified in the certificate.
- Ensuring Code Integrity: The signing process generates a hash of the code and encrypts it with the private key. During verification, the system recalculates the hash and compares it to the decrypted signature value using the public key. Any changes to the code result in hash mismatches, causing the signature validation to fail and indicating that the code has been altered.
- Enhancing User Trust: Operating systems and security software usually display warnings for unsigned or unknown publisher software. Using a code signing certificate removes such warnings (within trusted environments, or after manually adding ServBay’s CA to the trust chain), boosting user confidence when installing or running the software.
- Preventing Malware Spread: Code signing makes it easier for users to distinguish legitimate software from malware disguised as authentic applications, helping prevent the spread of harmful software.
Applying for a Code Signing Certificate via ServBay
ServBay simplifies the process of obtaining code signing certificates within your local environment.
Open the SSL Certificate Management Panel: In the ServBay app sidebar, click the "SSL Certificates" menu item.
Initiate a New Certificate Request: On the SSL certificate management page, click the "+" (Add) button at the top right.
Fill Out Certificate Information: On the "Request Certificate" page, you need to complete the following key information:
- Common Name: Enter your organization’s name or your personal name. For example:
ServBay, LLCorServBay Demo Developer. - Usage Purpose: Choose how you intend to use the certificate. Select
Code Signing. - Request Method: Choose how the certificate will be issued. Select
ServBay CAto use ServBay’s built-in certificate issuing system. - Issuer: Select which internal ServBay CA should issue this certificate. Usually, choose
ServBay User CA. - Algorithm: Choose the encryption algorithm for generating the key pair. Common options include
ECC(Elliptic Curve Cryptography) orRSA(Rivest-Shamir-Adleman). ECC typically offers higher security with shorter key lengths for the same security strength. - Key Length: Choose the key length for your selected algorithm. For ECC, e.g.,
384; for RSA, e.g.,2048or4096. Longer keys are more secure but may be slightly slower to process. - Password: Very important! Set a strong password to protect your private key. This password is needed both to export the certificate (the
.p12file) and to use it with code signing tools. Do not forget this password, as ServBay cannot recover a lost private key password for you. Choose a custom, secure password. (Note: The passwordServBay.devshown in screenshots is an example only—do not use this weak password in practice. Always select your own secure password.)
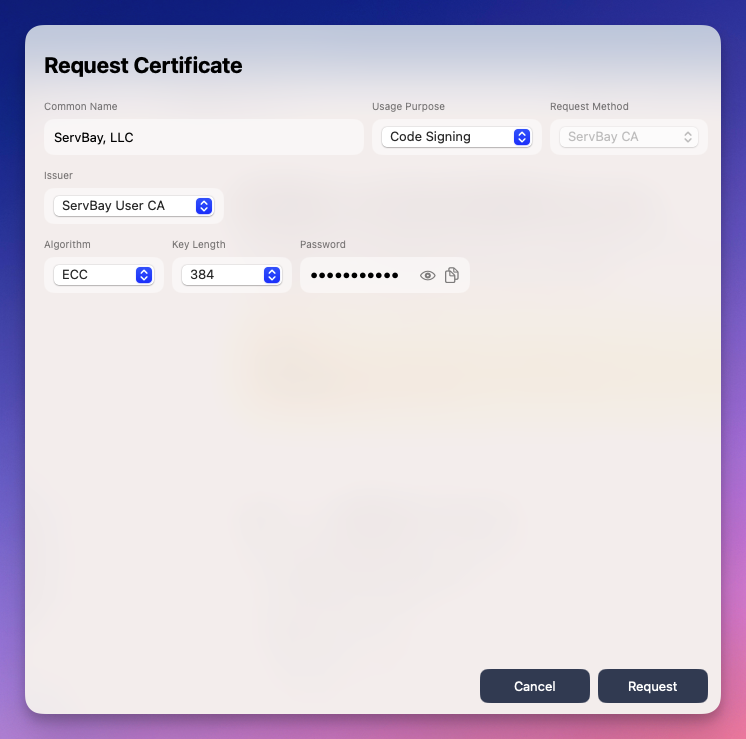 Sample screenshot—please fill with your actual information
Sample screenshot—please fill with your actual information- Common Name: Enter your organization’s name or your personal name. For example:
Submit Certificate Request: After completing and reviewing all information, click the "Request" button at the bottom of the page. ServBay will automatically issue your code signing certificate using the ServBay User CA you selected.
Exporting and Using the Certificate
Once you’ve successfully requested your code signing certificate, you’ll need to export it to a standard file format for use with various code signing tools. Certificates exported from ServBay are typically in .p12 format.
Go to the SSL Certificate Management Panel: Click "SSL Certificates" in the ServBay sidebar.
Locate Your Code Signing Certificate: In the certificate list, find the certificate you just applied for with "Code Signing" as its usage.
Click the Export Action: Click the export icon to the right of the certificate entry (usually a right-facing arrow icon).
Select Export Directory and Set Password: In the export dialog, choose the local directory where you want to save the certificate file. The exported file is typically in
.p12(PKCS#12) format, containing both your code signing certificate and its private key—so it's password-protected. You will need to enter the password you set when applying for the certificate to complete the export.Using the Certificate in Code Signing Tools: Import the exported
.p12file into your code signing tool. Different OSes and development environments use different tools:- macOS: Use the built-in
codesigncommand-line tool. You may first need to import the.p12file into macOS Keychain Access. - Windows: Use the
signtool.execommand-line tool included with the Windows SDK. You may first need to import the.p12file into the Windows Certificate Manager. - Other Platforms/Toolchains: Depending on your technology stack and build tools (e.g., Java’s
jarsigner, .NET’sSignTool, Go’s third-party signing tools, etc.), refer to the appropriate documentation for importing and signing procedures. Typically, you’ll need to specify the.p12file path and the private key password.
- macOS: Use the built-in
Once imported, you can use this certificate to digitally sign your code, applications, drivers, and more.
Example: Code Signing with the Certificate on macOS
The following example demonstrates how to use the codesign tool on macOS, along with a .p12 certificate exported from ServBay, to sign and verify a simple binary.
Assume you have already imported the .p12 file exported from ServBay into your macOS Keychain Access and entered the correct password during import.
bash
# 1. Create a simple C source file for signature testing
# Save the following content as test.c
cat <<EOF > test.c
#include <stdio.h>
int main() {
printf("Hello, ServBay Code Signing!\n");
return 0;
}
EOF
# 2. Compile the C file with gcc to produce a binary executable
# -o /tmp/test sets the output file name to /tmp/test
gcc test.c -o /tmp/test
echo "Compilation successful; /tmp/test generated"
# 3. List available certificates usable for code signing (Identity)
# -v for verbose output
# -p codesigning shows only code signing certificates
# Find your certificate's "Common Name" or its hash value (e.g., 99C183BC3796067FAFBA6F232D1C3C3425DAABDA)
security find-identity -v -p codesigning
# Example output might look like:
# 1) ABCDEF1234567890ABCDEF1234567890ABCDEF12 "Apple Development: Your Name (XYZ123)"
# 2) 99C183BC3796067FAFBA6F232D1C3C3425DAABDA "ServBay Demo Developer"
# 2 valid identities found
# Note the hash or Common Name ("ServBay Demo Developer") for your ServBay certificate
# 4. Sign the binary with your certificate
# -f forces signing (replaces existing signature if any)
# -s specifies signing identity, can be hash or Common Name (if unique)
# --timestamp adds a timestamp (optional, but recommended, to validate signature's time)
# /tmp/test is the binary to be signed
codesign -f -s "ServBay Demo Developer" --timestamp /tmp/test
# or use the hash:
# codesign -f -s "99C183BC3796067FAFBA6F232D1C3C3425DAABDA" --timestamp /tmp/test
echo "/tmp/test has been signed with code signing certificate"
# 5. Verify the signature
# -dvvv provides detailed signature info
codesign -dvvv /tmp/test
# Check the "Authority" field in the output—it should display your certificate info and ServBay CA chain
# Check "Signature size" and "CDHash"—these indicate the file is signed
# Check whether "Timestamp" is present
# Example verification output might include:
# Authority=ServBay Demo Developer
# Authority=ServBay User CA - ECC Code Signing
# Authority=ServBay Public CA - ECC Root
# Timestamp=Nov 7, 2024 at 18:26:48 (example date)
# 6. Attempt to modify the file, breaking the signature
# Write random data to the file, changing its hash value
echo "abcde" >> /tmp/test
echo "Contents of /tmp/test have been modified"
# 7. Verify the signature again
# Signature verification should now fail
codesign -dvvv /tmp/test
# Example output:
# /tmp/test: code object is not signed at all
# Or a similar error indicating the signature is invalid, as the file content no longer matches the signed hash.1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
Notes:
security find-identitylists certificates in the keychain available for a given purpose (likecodesigning). Find the identity for your imported ServBay certificate (usually its Common Name or hash).codesign -f -s "Your Identity"performs the signature. The--timestampoption contacts a timestamp server, associating the signature with a trusted time. Even after the certificate expires, as long as the certificate and timestamp were valid at signing, the signature is still considered valid.codesign -dvvvprovides detailed verification—including certificate validity, the trust chain, and whether the file’s content matches the signed hash.- The step where the file is modified and signature checked again demonstrates the core function of code signing: integrity verification. Any changes to the file will invalidate the signature.
Certificate Renewal
ServBay-issued code signing certificates are valid for a certain period (typically 800 days). Before the certificate expires, you can renew it in the ServBay SSL certificate management panel.
- Open the SSL Certificate Management Panel.
- Locate the Code Signing Certificate to be Renewed.
- Click the Renewal Action: Click the renewal icon (usually a circular arrow) on the right of the certificate entry.
- Confirm Renewal: After clicking the renewal button, ServBay will issue a new certificate, valid for 800 days from the current date.
Certificate Deletion
If you no longer need a code signing certificate, you can remove it from ServBay.
- Open the SSL Certificate Management Panel.
- Locate the certificate to delete.
- Click the Delete Action: Click the trash can icon to the right of the certificate entry.
- Confirm Deletion: In the confirmation dialog, select "Delete" and confirm your action. Note: Once deleted, the certificate cannot be recovered.
Frequently Asked Questions (FAQ)
Q: Are ServBay-issued code signing certificates free?
A: Yes, certificates issued by ServBay’s internal CA are a built-in feature of ServBay and incur no additional cost.
Q: Can I use ServBay-issued certificates to sign and distribute my commercial software to users?
A: No. ServBay-issued certificates are signed by its internal CA, not trusted by public operating systems or app stores. They are strictly for local development, testing, or controlled internal environments. For software distributed publicly, you must purchase a code signing certificate from a publicly trusted Certificate Authority.
Q: What if I forget the password set when exporting the .p12 file?
A: ServBay does not store your private key password. If the password is lost, the private key cannot be exported or used. You’ll need to delete the certificate and request a new code signing certificate.
Q: Can I add ServBay User CA to my operating system’s trust store?
A: Yes, you can typically export the ServBay User CA certificate and manually import it into your OS or browser's trust store.
Summary
ServBay’s code signing certificate feature makes it convenient for developers to test software signing and sign internal tools in a local environment. With this guide, you should now understand the basic process for applying, exporting, and using these certificates in ServBay. Remember, these certificates are mainly for development and testing—they are not suitable for scenarios that require public trust.
If you encounter any difficulties during the application or usage process, consult ServBay’s official documentation or seek help from the community.